6. Audit and Compliance
It is clear that the CSP will face a large number of requests from its customers to
prove that the CSP is secure and reliable. There a number of audit and
compliance considerations for both the CSP and the customer to consider
in cloud computing. First, which compliance framework should a CSP adopt
to satisfy its customers and manage its own risks? The customer base
will largely determine the framework that the CSP would choose. Most IT
service providers are adopting a combination of ITIL, ISO 27001, and
specific industry standards such as the Health Insurance Portability and
Accountability Act of 1996 (HIPAA) and the Payment Card Industry (PCI).
It is expected that the CSP will adopt the same approach.
It is possible that the adoption of cloud computing may impact an
organization’s Sarbanes-Oxley (SOX) program. At the moment, most
organizations are resisting putting any data relating to financial
reporting systems into cloud computing. However, email is often used as
the means for communicating the authorization or approval of a control
activity, and this may end up in the cloud. Alternatively, smaller
organizations with finite resources may use PaaS and thereby bring
software development life cycle controls into scope.
Many forms of reporting are available to satisfy these requests. The most
relevant standard for the CSP to adopt would be SysTrust, or eventually,
SAS 70, once new changes are made to this standard.
For the CSP to be successful it will be necessary to establish an
appropriate framework of processes and controls. This framework needs to
be comprehensive and globally accepted to meet the challenges of the
various industry verticals. Imagine if the CSP customer is a health care
provider or a bank. The requirements will be different for each and it
can be expensive for a CSP to meet the various industry
requirements.
A growing concept in the industry is the development of an IT
Governance, Risk, and Compliance (GRC) program. The intent of such a
program is to develop an IT uniformed compliance framework. A number of
tools are available today that can automate this process. Such tools
have:
A library of controls covering standards such as ISO 27001,
PCI, Control Objectives for Information and Related Technology
(COBIT), ITIL, the National Institute of Standards and Technology
(NIST), and many others
Built-in connectors to leverage existing security tools
deployed in the IT environment
A flexible, real-time reporting engine that can report on
various standards and organizational units
Figure 1 illustrates an overview
of the capabilities of an IT GRC program and its relationship to the
broader enterprise GRC. A large proportion of its function relates to
security, and such programs result in the adoption of compliance
dashboards that can be configured to various levels of management and
show real-time compliance and an indicator of where risk exists.
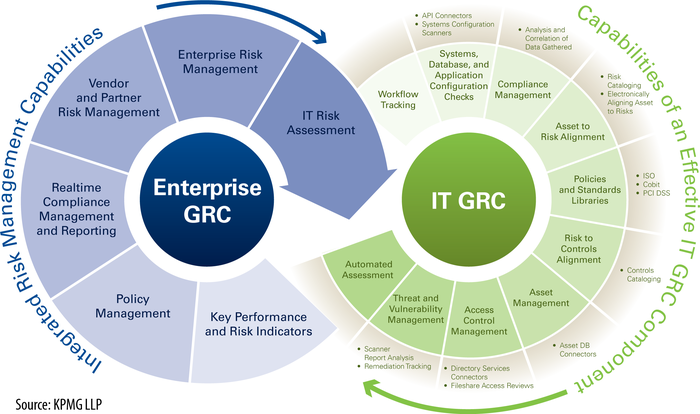
Such tools can report on specific organizational units against a
specific standard, or a combination of standards against a tailored
framework. This would allow a CSP to reduce its cost of compliance and
create a more sustainable solution. The adoption of IT GRC will allow
the CSP to deliver more custom reports to reflect the standards relevant
to the customer and in a timelier manner.
7. Security-As-a-[Cloud]-Service
Security-as-a-service is already well established in the nascent cloud computing
space. In fact, it is likely to continue to grow both in terms of market
share against traditionally delivered security capabilities and in terms
of depth of offerings. For example, not only is the relatively new
identity-as-a-service (IDaaS) a needed alternative for individual
organizations, but IDaaS will become even more desirable for growing
organizational types, such as increasingly multistatus organizations
(i.e., employees, contractors, interns, other companies’ employees, and
vendors, all working in the same shared workspace), co-opetition
(cooperative competition), and virtual organizations. Additionally,
other important security services could be outsourced and provided in a
cloud environment, such as logging, auditing, and security incident and
event management (SIEM).
Security-as-a-service is likely to see significant future growth
for two reasons. First, it is likely that a continuing shift in
information security work from in-house to outsourced will continue.
What started with email filtering and managed security services will
continue and expand as organizations look to reduce capital expenditures
(CapEx) further and increasingly concentrate on their core capabilities.
Second, several other information security needs are present for
organizations currently, but they will accelerate in need and complexity
with the growing adoption of cloud computing. That growing complexity
will further fuel the growth of SaaS. Specifically, we are referring to
two preventive (proactive) controls and two detective (reactive)
controls. The two proactive controls are also important to the growth of
cloud computing: identity management that is intercloud and scalable to
the cloud size, and (encryption) key management. Significant improvement
in both is needed for cloud computing, and that will make potential
solutions very valuable. The two reactive controls are needed for audit
and compliance purposes as well: scalable and effective SIEM, and data
leakage prevention (DLP). Trying to provide solutions to each of these
controls will be difficult and requires significant complexity that must
be hugely scalable and yet easy to use. However, all of these needs also
pose significant and growing opportunities for vendors as cloud
computing continues to grow in adoption.
8. Impact of Cloud Computing on the Role of Corporate IT
Almost certainly, many corporate IT departments will continue to be redefined by
this latest model of outsourcing. As with earlier outsourcing (e.g., to
large IT services firms such as CSC, EDS, and IBM Global Services, or
application development to China or India), use of collocation
facilities or application service providers (ASPs) and IT functions
previously done in-house are moving outside corporate IT departments.
With growing IT needs at the cost of growing complexity, many
organizations are deciding that IT is not a core competency for their
organizations and much of the IT work required to run today’s
organizations is being turned over to specialist companies. Cloud
computing is a further example of this.
However, cloud computing is in some respects also a repudiation of
traditional corporate IT departments. Business units are tired of
hearing CIOs and IT departments telling them that the costs of their
desired projects are excessively high and that there will be an
excessive time delay until those projects can be implemented. Part of
cloud computing’s appeal is the speed with which business units can be
up and running on their desired platform or application, along with the
perceived lower costs of “pay as you go” and lack of upfront capital
expenditures. As such, it really should be no surprise that the push for
the use of cloud computing in most organizations is coming from business
units and not from within IT. The long-standing tech mantra of better,
faster, cheaper has come home to roost for corporate IT departments.